File Access Permission in Linux
This Lecture teaches you the following topics:
- Authorization Levels in Linux
- Reading and setting file permissions.
Linux is a multi-user operating system which can be accessed by many users simultaneously.
Linux can also be used in mainframes and servers without any modifications. But this raises security concerns as an unsolicited or malign user can corrupt, change or remove crucial data.
Authorization Levels
For effective security, Linux divides authorization into 2 levels.
- Ownership
- Permission
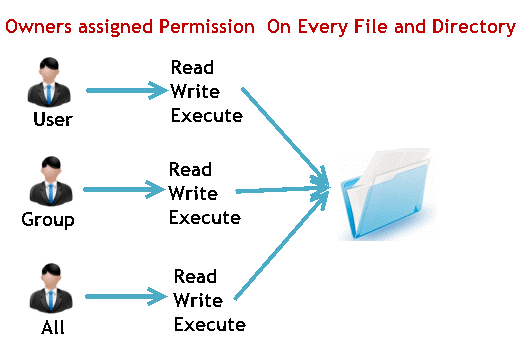
Ownership of Linux files
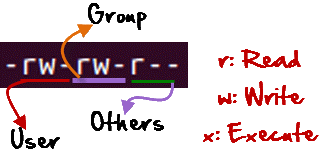
Every file and directory on your Unix/Linux system is assigned 3 types of owner, given below.
User
- A user is the owner of the file.
- By default, the person who created a file becomes its owner.
- A user is also sometimes called an owner.
Group
- A user- group can contain multiple users.
- All users belonging to a group will have the same access permissions to the file.
- Suppose you have a project where a number of people require access to a file.
- Instead of manually assigning permissions to each user, you could add all users to a group, and assign group permission to file such that only this group members and no one else can read or modify the files.
Other
- Any other user who has access to a file.
- This person has neither created the file, nor he belongs to a user group who could own the file.
- Practically, it means everybody else. when you set the permission for others, it is also referred as set permissions for the world.
Permissions
Every file and directory in your UNIX/Linux system has following 3 permissions .
Read:
- This permission give you the authority to open and read a file.
- Read permission on a directory gives you the ability to lists its content.
Write:
- The write permission gives you the authority to modify the contents of a file.
- The write permission on a directory gives you the authority to add, remove and rename files stored in the directory.
- Consider a scenario where you have to write permission on file but do not have write permission on the directory where the file is stored. You will be able to modify the file contents. But you will not be able to rename, move or remove the file from the directory.
Execute:
- In Windows, an executable program usually has an extension “.exe” and which you can easily run.
- In Unix/Linux, you cannot run a program unless the execute permission is set.
- If the execute permission is not set, you might still be able to see/modify the program code(provided read & write permissions set), but not run it.
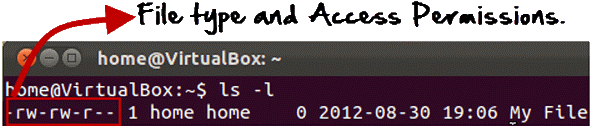
ls – l on terminal gives
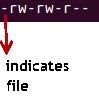
Here, the first ‘–‘ implies that we have selected a file.
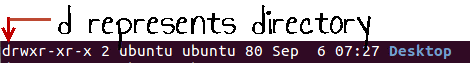
Else, if it were a directory, d would have been shown.
The characters are pretty easy to remember.
r = read permission
w = write permission
x = execute permission
– = no permission
- The first part of the code is ‘rw-‘. This suggests that the owner ‘Home’ can:

- Read the file
- Write or edit the file
- He cannot execute the file since the execute bit is set to ‘-‘.
By design, many Linux distributions like Fedora, CentOS, Ubuntu, etc. will add users to a group of the same group name as the user name. Thus, a user ‘tom’ is added to a group named ‘tom’.
- The second part is ‘rw-‘.It for the user group ‘Home’ and group-members can:
- Read the file
- Write or edit the file
- The third part is for the world which means any user. It says ‘r–‘.This means the user can only:
- Read the file
User Account File
User accounts are defined in the /etc/passwd file.
Group Account File
Groups are defined in the /etc/group file.
Users Password File
These files are modified along with /etc/shadow which holds information about the user’s password.
Id Command
Id command is used to find out user and group names and numeric ID’s (UID or group ID) of the current user or any other user in the server.
This command is useful to find out the following information as listed below:
- User name and real user id.
- Find out the specific Users UID.
- Show the UID and all groups associated with a user.
- List out all the groups a user belongs to.
- Display security context of the current user.
Option with Id command

chmod command is used to change file mode.Change File Mode (Permissions)
- Only the file’s owner or the super-user can change the mode of a file or directory.
- chmod supports two distinct ways of specifying mode changes:
-
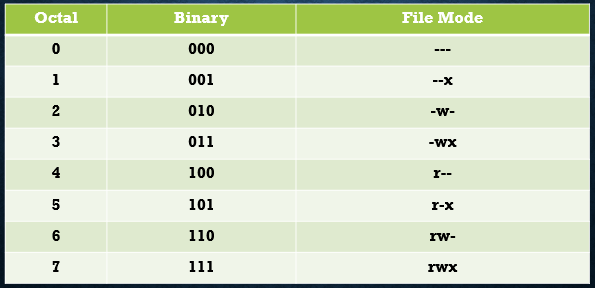
- octal number representation(each digit in an octal number represents three binary digits)
- symbolic representation.
File Mode in octal and binary representation
Example
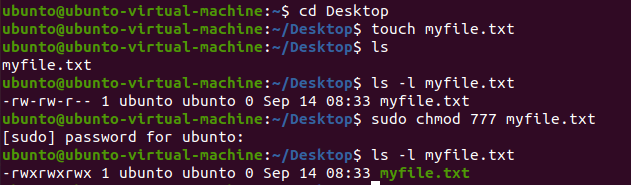
- Press CTRL+ALT+T Keys to open Terminal.
- Go to the Desktop directory using cd command.
- In Desktop directory, we create a text file “myfile.txt” using touch command
- Read its current permissions using ls command.
- Now, we change the permission of myfile.txt and set it to 777 that is everyone can read, write and execute the file.
chmod using symbolic notation
Symbolic notation is divided into three parts:
- who the change will affect,
- which operation will be performed,
- what permission will be set.
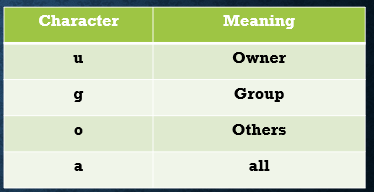
To specify who is affected, a combination of the characters “u”, “g”, “o”, and “a” is used as follows:
symbolic notation = , +, –
If no character is specified, “all” will be assumed.
The operation may be a “+” indicating that a permission is to be added.
a “-” indicating that a permission is to be taken away.
a “=” indicating that only the specified permissions are to be applied and that all others are to be removed.
Example
u+x,go=rx
- Add execute permission for the owner and set the permissions for the group and others to read and execute.
- Multiple specifications may be separated by commas.
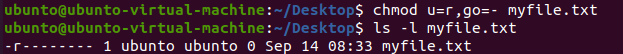
For example, we change the permissions of myfile.txt using symbolic codes.
Now we make it readable only to the user while the rest cannot read, write or execute the file.
Related Links to Operating System topics
Operating system Course content
- Operating System-Functions and History
- Generations of Operating System
- Functions of an Operating System
- Components of Operating System
- Types of Operating System
- Services of Operating System
- Properties of Operating System
- Processes in Operating System
- Process Scheduling in Operating System
Lab Practice Task
- Introduction to Linux Ubunto
- Installation with virtual Box
- Writing Linux Commands
- Navigation in File System and Directory Management in Ubunto using CLI
- File Handling and I/O Redirection In Ubunto
- File Access Permission in Linux
- Text Processing Tools and Basic System Configuration Tools in Linux
- Package Management in Linux
- How to manage processes in Linux
- Compiling and Executing C++ programs in Linux
- System Calls
- Introduction To Shell Programming
#Operating System complete course #Operating System past paper #Operating System-project #Computer Science all courses #operating system Problem with source code#University Past Paper #Programming language #Question paper #old paper #Operating System-Functions and History #Generations of Operating System #Functions of an Operating System #Components of Operating System #Types of Operating System #Services of Operating System #Properties of Operating System #Processes in Operating System #Process Scheduling in Operating System #Introduction to Linux Ubunto #Installation with virtual Box #Writing Linux Commands #Navigation in File System and Directory Management in Ubunto using CLI #File Handling and I/O Redirection In Ubunto #File Access Permission in Linux #Text Processing Tools and Basic System Configuration Tools in Linux #Package Management in Linux #How to manage processes in Linux #Compiling and Executing C++ programs in Linux #System Calls #Introduction To Shell Programming

