Cybersecurity is the combination of technologies and procedures used to safeguard networks, devices, programs, and data from assault, deterioration, and illegal access. Information technology security is another name for cyber security. Cybersecurity is the activity of identifying and mitigating risks connected with digital systems’ susceptibilities and threats. Computers that are connected to the internet or to other equipment, such as processors, input devices, output devices, and networking connections, are referred to as “cyber”. Our organization’s information, private data, financial data, and a variety of other forms of information are among the data on our computer that, if accessed by unauthorized methods, can have unfavorable consequences.
Importance of cybersecurity:
Cybersecurity measures are crucial to the value and quality of a system because vulnerabilities (flaws or weaknesses) in software, firmware, or hardware expose systems to cyber-attacks. If attackers gain unauthorized access to a weak system with sensitive data, they can steal and sell your information, which results in fraudulent purchases and activity. These vulnerabilities may arise from programming inefficiencies or misuse of hardware.
Types of cybersecurity:
Following are some of the important types of cybersecurity:
- Application security
- Cloud security
- Critical infrastructure security
- Information security (info security)
- Network security
Application security:
App security is a sort of protection for apps that guards against online threats and takes into consideration any software flaws that might make users vulnerable. Application security is essential to the software’s dependability and performance.
Cloud security:
A portion of IT called cloud security deals with managing risks and problems associated with a cloud- based network. It also involves locating and putting solutions into practice, primarily wirelessly. Security experts rely on the cloud for memory, security, and any potential flaws that need to be fixed.
Critical infrastructure security:
The public often uses critical infrastructure security, a high-tech kind of security, to safeguard the assets, systems, and networks that belong to the general populace, neighborhood, city, or nation. This area of cybersecurity focuses on national defense and infrastructure that is held by the government.
Information security (InfoSec):
Information security involves keeping data safe and avoiding unauthorized access to the collection of personal information using contemporary applications (WhatsApp, Facebook, Instagram). Information security addresses the confidentiality, integrity, and availability issues that impact how well a system handles or stores information.
Network security:
Network security protects a business’s infrastructure’s dependability and security. Network security places a strong emphasis on network integrity to guarantee that the system is impenetrable by internet-based cyberattacks.
Common cybersecurity threats:
Attackers on our systems frequently have financial gain in mind when they do so. However, some malicious individuals make attempts to steal or destroy data out of political motivations, as an internal threat to the firm they work for, for their own company’s advantage, or just for fame. A security system can be attacked or hacked in a variety of ways. The following list includes five typical assault methods:
Password attacks:
Among the most popular ways to fraudulently enter a system is by password cracking. Attackers employ a variety of strategies to get passwords for sensitive or personally identifiable information. Brute force attacks are occasionally used by password crackers. To put it another way, they attempt every password until one match. They could even employ more complex methods like dictionary attacks, where a software tries a lot of widely used passwords until it finds one that matches.
Phishing attacks:
One of the most persistent risks to personal systems is phishing assaults. This procedure entails sending a list of user’s bulk emails that appear to be from reliable sources. Malicious links in these emails have the potential to install malware and give unauthorized access sensitive data when they are clicked. These assaults can also occur via the phone (also known as vishing), on websites, or on social media.
DOS attack:
Denial-of-service assault is referred to as DOS. A system is under assault when software or a set of devices try to overwhelm it, preventing it from functioning correctly and accomplishing its intended function.
Man-in-the-middle attack:
A man-in-the-middle attack happens when an attacker uses a network’s security flaws to interpose themself in a two-machine conversation. They then keep an eye on the IP packets that are being exchanged. They can be able to intercept important information in this way.
Malware:
Ransomware assaults are carried out by programs that are intended to take advantage of a system or behave maliciously toward a person or institution. Malware assaults come in a wide variety of forms, including spyware, viruses, trojan horses, worms, and ransomware. Most of this kind of malware automatically installs itself and takes advantage of flaws in the system to infect other computers, grab certain data, or just disrupt or harm a device.
The growing importance of cybersecurity in industry:
It is impossible to exaggerate the significance of cybersecurity for organizations in the current digital era. Because of the growing reliance on technology and the internet, cyber dangers are evolving and multiplying, posing a serious risk to companies of all kinds. Here are some main justifications for why organizations must prioritize cybersecurity:
Protecting sensitive data:
Protecting sensitive data is one of the main reasons firms should engage in cybersecurity. This includes private intellectual property, financial data, and consumer information. Data breaches caused by cyberattacks can have serious repercussions, including monetary losses and reputational harm.
Maintaining business operations:
Your company’s activities may be affected by a cyberattack, which might result in downtime and lost production. Making sure your business has a solid cybersecurity policy in place reduces the possibility of expensive interruptions and aids in maintaining the continuity of your operations.
Regulatory complains:
Organizations must adhere to several rules that mandate strict security protocols to safeguard the data of their clients. Heavy fines and penalties may be imposed for breaking these rules. Businesses may avoid potential legal problems by staying compliant with these requirements by investing in cybersecurity.
Building trust with customers:
Consumers are getting more and more conscious of the value of safeguarding their data. Businesses may boost consumer trust and foster long-lasting connections by displaying a strong commitment to cybersecurity.
Educational and training importance:
Teams benefit from training when they learn how to make better passwords for a variety of applications, including social networking sites, protected data files, and email accounts. Teams who are knowledgeable about cybersecurity also appreciate the value of routine password updates for keeping networks and accounts safe.
Ways to improve security:
Recent years have seen a tremendous increase in cloud use, leaving little time for cybersecurity to follow up. The cloud security sector is growing quickly due to various cloud vulnerabilities as well as poorly protected distant work settings, from which cloud services are often accessible. According to Gartner, the cloud security market will expand significantly between 2023 and 2024. Following are some ways to improve cyber security:
Using zero trust in combination with VPN:
Scalability issues with virtual private networks might arise. In contemporary hybrid contexts, VPN technology could be vulnerable to hacking attempts and security flaws. In comparison, the zero-trust strategy is safe and expandable. By the conclusion of the 2024 fiscal year, the Biden administration in the US has mandated that federal agencies [PDF] adhere to zero-trust standards.
Augmenting supply chain infrastructure:
In 2023 we will see the development of current cybersecurity supply chain risk management techniques as well as the pursuit of novel supply chain security measures by cybersecurity professionals. Many of these examples of espionage, state-sponsored cyberattacks, and geopolitical unrest that have an impact on the global supply chain are the reasons for this. For instance, in February 2022, Russia targeted the technology used to manage crucial Ukrainian infrastructure. By 2025, 45% of firms, or more than three times as many as in 2021, are expected to face assaults on their software supply chains, according to Gartner.
Tools and Comparison across multiple Cyber Technologies:
The following table shows the tools being used in cyber industry and their usages.
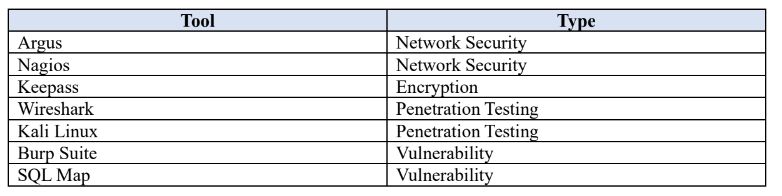
Whether you are a professional or just starting in the field of cyber security, basic knowledge of all these tools is necessary to progress and increase you know how about cyber security.
Career in cyber security:
Depending on your degree of experience and area of expertise, cyber security provides a range of career possibilities. Cyber Security is a very vast field with multiple pathways and options for IT professionals. You may work as an analyst/engineer, network administrator, programmer, or data analyst, among many other professions.
Some professions are necessary, while others are viable if they correspond to your area of expertise in security, such as finance or computer science. Cybersecurity is the best choice for you if you’re seeking a lucrative job because it’s still relatively new and will only continue to expand. The future certainly needs a lot of cyber security professionals be it to expand & improve existing infrastructure or help create central smart cities across world. A cyber professional is certainly needed to make sure the system is safe and secure from external interference and can run smoothly. Users need to be very careful about how they use and share their personal information so they can ensure the integrity of sensitive data is not compromised.
Cyber security is involved in every area of our life now be it with protecting our personal information or national grid systems or advanced medical devices. Everything needs to be fully secured before it is available and safe to use for user. The next industrial revolution is certainly going to be in AI and IoT connectivity and it does raise concerns about how system will be safeguarded against viruses and malicious attacks. A cyber analyst is perfectly placed to use the learned skillsets and help in creating a better environment for humanity. Numerous steps can be taken to train the upcoming generation in cyber security by including new curriculum related to cyber threats in universities. Training program can be added related to penetration testing and firewall testing with example of real-life students PC. This will certainly peak students’ interest in this upcoming in demand skill.
Conclusion:
In conclusion, cyber security is very essential and crucial part of our live and we need to raise awareness related to it. Its importance will certainly increase with time and so will its effects. It is surely challenging, and companies need to be robust enough to handle and adopt to rapidly changing digital landscape and it security.


