Networking Applications
A computer network is a combination of devices (computers and peripherical devices) that are connected together for the purpose of data or resource sharing.
A computer network is a collection of interconnected computers and other devices that can communicate and share resources with each other. These networks are used to enable data and information exchange among devices, allowing them to work together efficiently and effectively. Computer networks can vary in size and complexity, from small local networks in homes or offices to large global networks.
Networking Applications
Networking applications are software programs or services that use computer networks to facilitate communication, data sharing, and collaboration among users and devices. These applications leverage the capabilities of computer networks to enable various forms of interaction and information exchange like
- Email: Email applications allow users to send and receive messages electronically over the internet or an organization’s internal network. Popular email clients include Microsoft Outlook, Gmail, and yahoo.
- Instant Messaging (IM): IM applications enable real-time text-based or multimedia communication between individuals or groups. Examples include WhatsApp and Facebook Messenger
- Video Conferencing: Video conferencing apps like Zoom, Microsoft Teams, and Skype allow users to conduct face-to-face meetings and presentations over the internet
- Voice over IP (VoIP): VoIP applications, such as Skype enable audio, video call that is lower in cost as compared to traditional phone service.
- Social Networking: Social networking platforms like Facebook, Twitter, and LinkedIn connect users globally, allowing them to share updates, photos, and messages with friends, colleagues, and the public.
- File Sharing: File-sharing applications, including Dropbox, and Google Drive, allow users to share and collaborate on files and documents over the network.
- Remote Desktop and Collaboration Tools: Applications like TeamViewer, AnyDesk, and Remote Desktop Protocol (RDP) enable remote access to computers and facilitate collaboration among users in different locations.
- Cloud Services: Cloud-based networking applications, such as Amazon Web Services (AWS) and Microsoft Azure, provide scalable and on-demand resources for hosting websites, applications, and data storage.
- Web Browsers: Web browsers like Google Chrome, Mozilla Firefox, and Microsoft Edge are essential networking applications used to access websites and web-based services.
- Network Monitoring and Management Tools: These applications, such as Wireshark, Nagios, and SolarWinds, help network administrators monitor, troubleshoot, and manage network performance and security.and many more ….
Telecom Industry
The telecommunications industry is a vast and ever-evolving sector that encompasses the technology, services, and infrastructure related to the transmission of voice, data, and multimedia over long distances. It plays a crucial role in connecting people, organizations, and devices worldwide. Here are some key aspects of the telecom industry:
- Telecommunication Services: Telecom companies provide various services to consumers and businesses, including voice calls, messaging (SMS and MMS), internet access (broadband and mobile data), and video streaming. These services are delivered through wired and wireless networks.
- Telecom Infrastructure: Telecom infrastructure includes the physical and technical components that enable communication. This includes network equipment like switches, routers, base stations, and data centers, as well as the network of cables, fiber optics, and wireless towers that transmit signals.
- Wireline and Wireless Networks: The industry is divided into two main segments: wireline and wireless networks. Wireline networks use physical cables (e.g., fiber-optic, copper) for data transmission, while wireless networks rely on radio waves and cellular technology. Mobile networks, such as 4G and 5G, fall under the wireless category.
- Internet Service Providers (ISPs): ISPs are a subset of the telecom industry that primarily provides internet access to homes and businesses. They offer various types of connections, including DSL, cable, fiber-optic, and satellite.
and many more like Telecom Equipment Manufacturers, Regulatory Bodies, Global Connectivity, Emerging Technologies, Competition and Consolidation, Customer Services, Telecom Policies, Security Challenges, Future Trends
Basic characteristics of a Computer Network
Security Most businesses nowadays rely on computers, which are accessed through networking. As a result, if computer network technology is not robust and secure, unauthorized access to the company’s critical data might be possible.
Reliability Computer networks are very reliable tools, and users can easily interconnect their devices with their help. Their networking experience remains consistent even if users need to print, check messages, attend a meeting, or access data from another computer.
Scalability refers to the ability to scale up in response to changing needs while maintaining high performance. The internet is the best example of scalability; many new users connect via the internet and communicate with other devices, but our network still works properly.
Flow of Data Users can access and transmit data such as files, documents, and other types of information with the help of computer networking.
and High performance, Fault tolerance, Quality of Service, Compatible With Hardware and Software Components are also network characteristics.
Types of networks
Local Area Network (LAN):
-
- Scope: Limited geographical area (e.g., home, office, campus).
- Characteristics: High data transfer rates, typically using Ethernet or Wi-Fi.
- Purpose: Sharing resources (e.g., printers, files) and providing local network services.
Wide Area Network (WAN):
-
-
- Scope: Covers a large geographical area (e.g., across cities, countries).
- Characteristics: Slower data transfer rates over longer distances.
- Purpose: Connecting LANs, often using public or private telecommunications services.
-
Metropolitan Area Network (MAN):
-
- Scope: Intermediate between LAN and WAN, typically within a city.
- Characteristics: Faster than WANs but with a limited geographic scope.
- Purpose: Connecting multiple LANs within a city or metropolitan area.
Personal Area Network (PAN):
- Scope: Very short range (a few meters).
- Characteristics: Typically wireless connections (e.g., Bluetooth).
- Purpose: Connecting personal devices like smartphones, tablets, and peripherals.
and many more like, Home Area Network, Campus Area Network, Virtual Private Network, Intranet, Extranet, Cloud Network, Sensor Networks, Ad Hoc Network, Peer-to-Peer (P2P) Network
Network Topologies
Network topology refers to the physical or logical arrangement of devices and connections in a computer network. Different network topologies have distinct in terms of cost, scalability, reliability, and ease of maintenance.
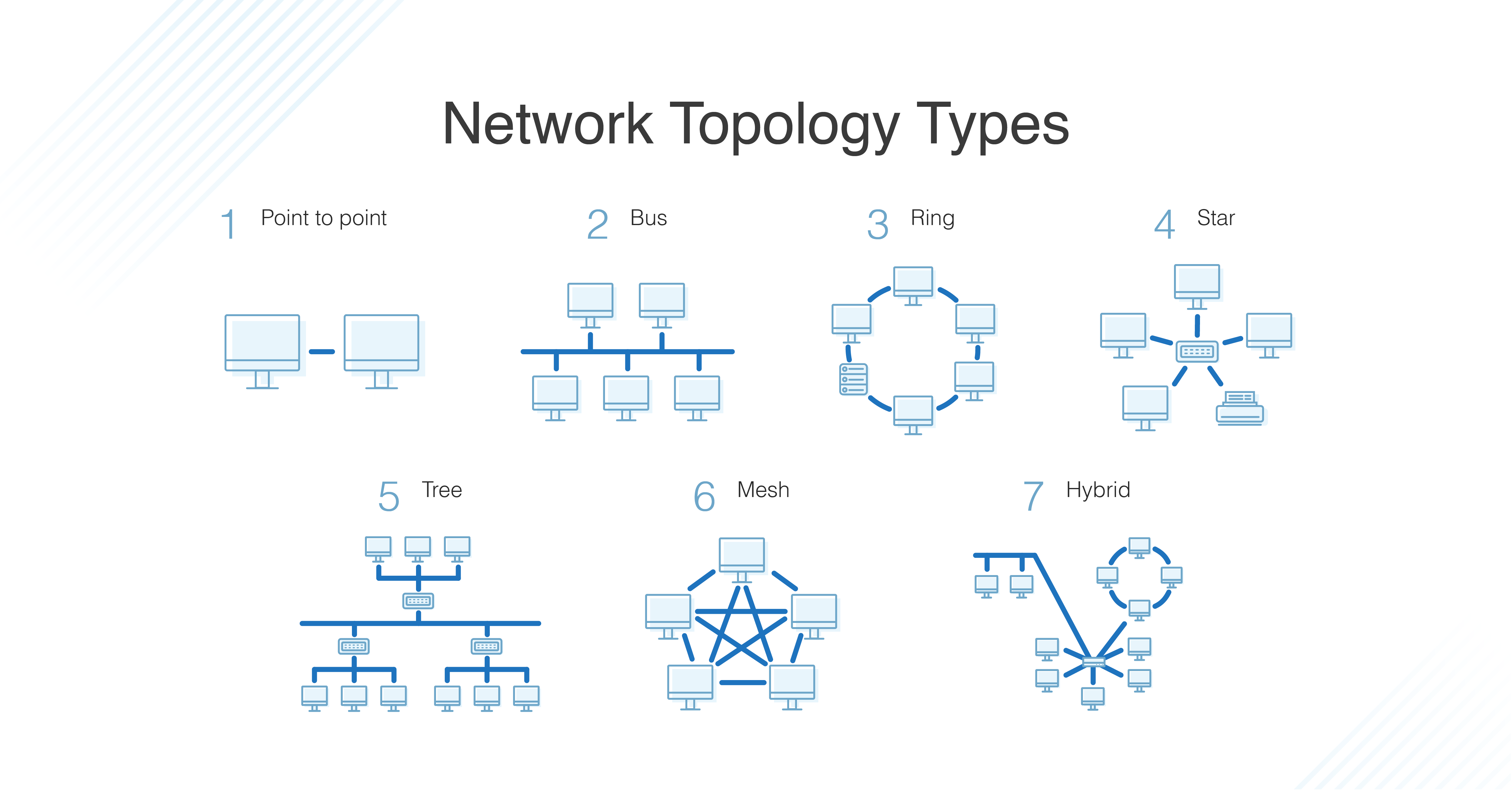
Bus Topology:
-
- Physical: All devices are connected to a single central cable (the bus).
- Characteristics: Simple, inexpensive, but prone to single point of failure.
- Common Use: Small networks and educational settings.
Star Topology:
-
- Physical: All devices are connected to a central hub or switch.
- Characteristics: Robust and easy to manage, but the hub/switch is a single point of failure.
- Common Use: LANs in offices and homes.
Ring Topology:
-
- Physical: Devices are connected in a closed-loop, with each device connecting to exactly two others.
- Characteristics: Data travels in a unidirectional or bidirectional manner, depending on the implementation.
- Common Use: Token Ring networks (less common today) and some fiber-optic networks.
Mesh Topology:
-
- Physical: Every device is connected to every other device.
- Characteristics: Extremely fault-tolerant, redundant, and scalable, but costly and complex to set up.
- Common Use: Critical infrastructure and data centers.
Tree Topology, Hybrid Topology, Point-to-Point Topology, Star-Bus Topology, Daisy Chain Topology, Fully Connected Topology are also network topology types
Network Architectures
Network architectures define the structure and organization of computer networks. Key architectures include client-server, which centralizes resources; peer-to-peer, where devices share resources equally; three-tier, dividing functionality into presentation, application, and data layers; layered, which organizes functions in a modular way; service-oriented, based on reusable services; microservices, with small, independent services; hierarchical, in large-scale networks; software-defined, separating control and data planes; fog and edge computing, for low-latency processing; and content delivery networks, optimizing content delivery. Each architecture suits specific network purposes and requirements, such as scalability, performance, and flexibility.
Network Size & Coverage Area
Network size and coverage area refer to the extent and scale of a computer network. Network size involves the number of devices or nodes connected, ranging from small setups like home networks to massive corporate networks with thousands or even millions of devices. Coverage area defines how far-reaching the network is, with Local Area Networks (LANs) confined to a limited geographical area, Wide Area Networks (WANs) spanning larger regions, and Metropolitan Area Networks (MANs) falling in between.
The scale of a network impacts its performance, scalability, and complexity. Smaller networks are suitable for personal and small business needs, while larger networks are vital for complex operations like cloud computing and global internet services. Network size also influences factors like latency, security, redundancy, and management requirements, with larger networks often necessitating advanced measures to ensure reliability and data protection. The choice of network size and coverage area depends on specific use cases, budget constraints, and the scale of operations.

