Hacking
WHAT IS NETWORK SECURITY?
- Security is much larger than just packets, firewalls, and hackers. Security includes:
–Policies and procedures
–Liabilities and laws
–Human behavior patterns
–Corporate security programs and implementation
–Technical aspects- firewalls, intrusion detection systems, proxies, encryption, antivirus software, hacks, cracks, and attacks
- Understanding hacking tools and how attacks are carried out is only one piece of the puzzle.
ATTACKS
THERE ARE MANY TYPES OF ATTACKS
- SPOOFING ATTACK
- TELNET BASED ATTACK
- DOS (Daniel of service) ATTACK
- PING OF DEATH
- DISTRIBUTED DOS ATTACK
- MAILBOMBS
NEED FOR SECURITY
- SOME EXELLENT SOFTWARE CAN PROVIDE YOU BEST SECURITY
- LIKE
- TROJAN
- FIREWALL
TROJAN
- WINDOWS TROJANS ARE SMALL ASPECT OF WINDOWS SECURUTY
- TROJAN IS UNOTHORIZED PROGRAM CONTAINED WITHIN A LEGIMATE PROGRAM
- THIS PROGRAM PERFORMS FUNCTION UNKNOWN BY USER
FIREWALL
FIREWALL IS ANY DEVICE USED TO PREVENT OUTSIDERS FROM GAINING ACCESS TO YOUR NETWORK
TYPES OF FIREWALLS
- PACKET FILTER
- APPLICATION PROXY
- PACKET INSPECTION
Common Steps for Attackers
Reconnaissance
–Intelligent work of obtaining information either actively or passively
–Examples:
- Passively: Sniffing Traffic, eavesdropping
- Actively: Obtaining data from American Registry for Internet Numbers (ARIN), whois databases, web sites, social engineering
Scanning
–Identifying systems that are running and services that are active on them
–Examples: Ping sweeps and port scans
- Gaining Access
–Exploiting identified vulnerabilities to gain unauthorized access
–Examples: Exploiting a buffer overflow or brute forcing a password and logging onto a system
- Maintaining Access
–Uploading malicious software to ensure re-entry is possible
–Example: Installing a backdoor on a system
- Covering Tracks
–Carrying out activities to hide one’s malicious activities
–Example: Deleting or modifying data in a system and its application logs
Modes of Hacker Attack
- Over the Internet
- Over LAN
- Locally
- Offline
- Theft
- Deception
Spoofing
Definition:
An attacker alters his identity so that some one thinks he is some one else
–Email, User ID, IP Address, …
–Attacker exploits trust relation between user and networked machines to gain access to machines
Types of Spoofing:
1.IP Spoofing:
2.Email Spoofing
3.Web Spoofing
IP Spoofing – Flying-Blind Attack
Definition:
Attacker uses IP address of another computer to acquire information or gain access

IP Spoofing – Source Routing
Definition:
Attacker spoofs the address of another machine and inserts itself between the attacked machine and the spoofed machine to intercept replies

Email Spoofing
Definition:
Attacker sends messages masquerading as some one else
What can be the repercussions?
Types of Email Spoofing:
1.Create an account with similar email address
–[email protected]: A message from this account can perplex the students
2.Modify a mail client
–Attacker can put in any return address he wants to in the mail he sends
3.Telnet to port 25
–Most mail servers use port 25 for mails. Attacker logs on to this port and composes a message for the user.
Web Spoofing
- Basic
–Attacker registers a web address matching an entity e.g. votebush.com, geproducts.com, gesucks.com
- Man-in-the-Middle Attack
–Attacker acts as a proxy between the web server and the client
–Attacker has to compromise the router or a node through which the relevant traffic flows
- URL Rewriting
–Attacker redirects web traffic to another site that is controlled by the attacker
–Attacker writes his own web site address before the legitimate link
- Tracking State
–When a user logs on to a site a persistent authentication is maintained
–This authentication can be stolen for masquerading as the user
Web Spoofing – Tracking State
- Web Site maintains authentication so that the user does not have to authenticate repeatedly
- Three types of tracking methods are used:
1.Cookies: Line of text with ID on the users cookie file
–Attacker can read the ID from users cookie file
2.URL Session Tracking: An id is appended to all the links in the website web pages.
–Attacker can guess or read this id and masquerade as user
3.Hidden Form Elements
–ID is hidden in form elements which are not visible to user
–Hacker can modify these to masquerade as another user
Session Hijacking
Definition:
Process of taking over an existing active session
Modus Operandi:
1.User makes a connection to the server by authenticating using his user ID and password.
2.After the users authenticate, they have access to the server as long as the session lasts.
3.Hacker takes the user offline by denial of service
4.Hacker gains access to the user by impersonating the user
Session Hijacking
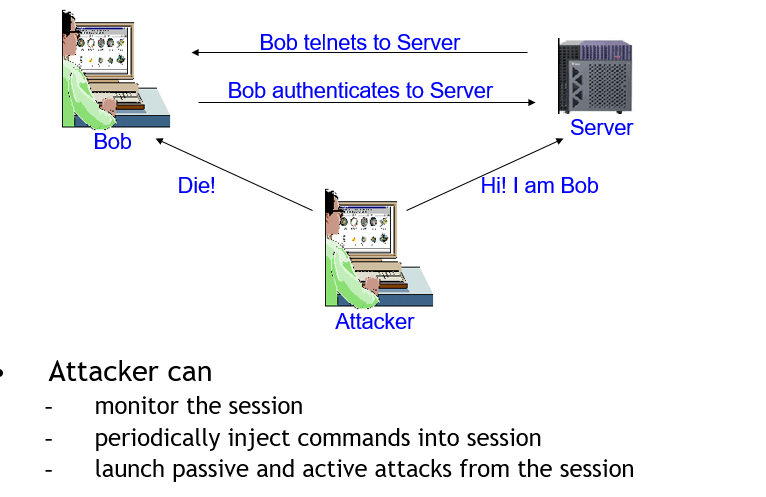
Session Hijacking – How Does it Work?
- Attackers exploit sequence numbers to hijack sessions
- Sequence numbers are 32-bit counters used to:
–tell receiving machines the correct order of packets
–Tell sender which packets are received and which are lost
- Receiver and Sender have their own sequence numbers
- When two parties communicate the following are needed:
–IP addresses
–Port Numbers
–Sequence Number
- IP addresses and port numbers are easily available so once the attacker gets the server to accept his guesses sequence number he can hijack the session.
Denial of Service (DOS) Attack
Definition:
Attack through which a person can render a system unusable or significantly slow down the system for legitimate users by overloading the system so that no one else can use it.
Types:
1.Crashing the system or network
–Send the victim data or packets which will cause system to crash or reboot.
2.Exhausting the resources by flooding the system or network with information
–Since all resources are exhausted others are denied access to the resources
3.Distributed DOS attacks are coordinated denial of service attacks involving several people and/or machines to launch attacks
Types:
1.Ping of Death
2.SSPing
3.Land
4.Smurf
5.SYN Flood
6.CPU Hog
7.Win Nuke
8.RPC Locator
9.Jolt2
10.Bubonic
11.Microsoft Incomplete TCP/IP Packet Vulnerability
12.HP Openview Node Manager SNMP DOS Vulneability
13.Netscreen Firewall DOS Vulnerability
14.Checkpoint Firewall DOS Vulnerability
Buffer Overflow Attacks
- This attack takes advantage of the way in which information is stored by computer programs
- An attacker tries to store more information on the stack than the size of the buffer
How does it work?

- Programs which do not do not have a rigorous memory check in the code are vulnerable to this attack
- Simple weaknesses can be exploited
–If memory allocated for name is 50 characters, someone can break the system by sending a fictitious name of more than 50 characters
- Can be used for espionage, denial of service or compromising the integrity of the data
Examples
–NetMeeting Buffer Overflow
–Outlook Buffer Overflow
–AOL Instant Messenger Buffer Overflow
–SQL Server 2000 Extended Stored Procedure Buffer Overflow

