Ethical Hacking
Ethical Hacking and Hacker
Objectives
Ethical hacking
- What you can do legally as an ethical hacker
- What you cannot do as an ethical hacker
Hacker and Ethical hacker
- Hackers
–Access computer system or network without authorization
–Breaks the law; can go to prison
- Ethical hacker
–Performs most of the same activities but with owner’s permission
–Employed by companies to perform penetration tests
Penetration test vs. Security test
- Penetration test
–Legal attempt to break into a company’s network to find its weakest link
–Tester only reports findings
- Security test
–More than an attempt to break in; also includes analyzing company’s security policy and procedures
–Tester offers solutions to secure or protect the network
- Programming languages used by experienced penetration testers
–Practical Extraction and Report Language (Perl)
–C
- Tiger box
–Collection of OSs and hacking tools
–Helps penetration testers and security testers conduct vulnerabilities assessments and attacks
Penetration-Testing Methodologies
- Penetration-Testing Methodologies
–White box model
–Black box model
–Gray box model
- White box model
–Tester is told everything about the network topology and technology
–Tester is authorized to interview IT personnel and company employees
–Makes tester job a little easier
- Black box model
–Company staff does not know about the test
–Tester is not given details about the network
- Burden is on the tester to find these details
–Tests if security personnel are able to detect an attack
- Gray box model
–Hybrid of the white and black box models
–Company gives tester partial information
Certification Programs for Network Security Personnel
- Penetration testers need to have
–the technical skills
–good understanding of networks
–the role of management in an organization.
- Network security certification programs
–Certified Ethical Hacker (CEH)
–OSSTMM Professional Security Tester (OPST)
–Certified Information Systems Security Professional (CISSP)
–Global Information Assurance Certification (GIAC)
- Certifications that help prepare for these certifications
–CompTIA Security+
–Network+
Certified Ethical Hacker (CEH)
- Developed by the International Council of Electronic Commerce Consultants (EC-Council)
–Based on 21 domains (subject areas)
–Web site: www.eccouncil.org
–Red team: Composed of people with varied skills
- Conducts penetration tests
OSSTMM Professional Security Tester (OPST)
- Designated by the Institute for Security and Open Methodologies (ISECOM)
–Based on the Open Source Security Testing Methodology Manual (OSSTMM)
–Consists of 5 domains
–Web site: www.isecom.org
Certified Information Systems Security Professional (CISSP)
- Issued by the International Information Systems Security Certifications Consortium (ISC2)
–Usually more concerned with policies and procedures
–Consists of 10 domains
–Web site: www.isc2.org
SANS Institute
- SysAdmin, Audit, Network, Security (SANS)
–Offers certifications through Global Information Assurance Certification (GIAC)
–Top 20 list
- One of the most popular SANS Institute documents
- Details the most common network exploits
- Suggests ways of correcting vulnerabilities
–Web site: www.sans.org
Objectives
- Ethical hacking
- What you can do legally as an ethical hacker
- What you cannot do as an ethical hacker
What You Can Do Legally
- As an ethical hacker, be aware of what is allowed and what is not allowed
–Laws involving technology change as rapidly as technology itself
–Find what is legal for you locally
- Laws change from place to place
- Some hacking Tools on your computer might be illegal to possess
–Contact local law enforcement agencies before installing hacking tools
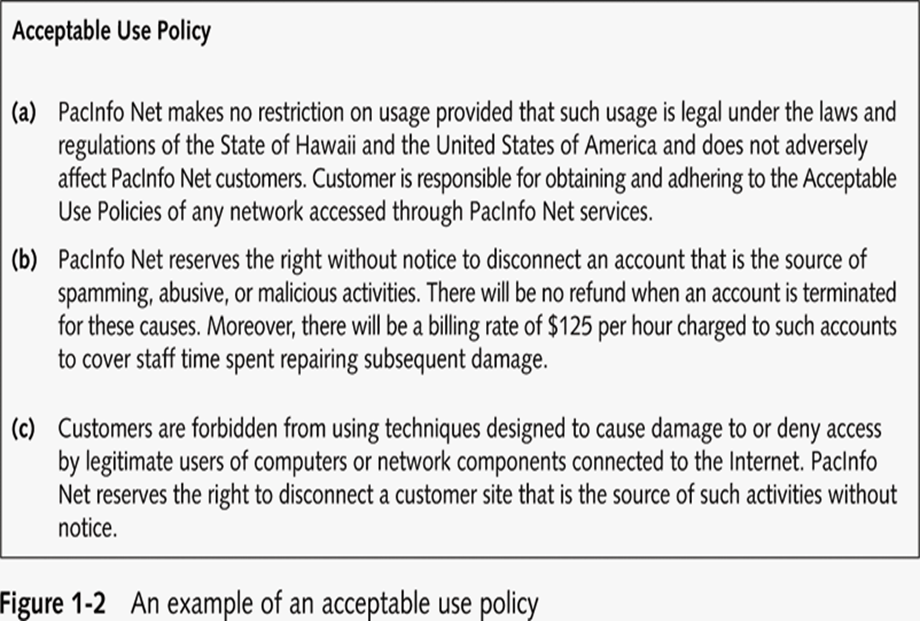
Is Port Scanning Legal?
- Federal Government does not see it as a violation
–Allows each state to address it separately
–Some states deem it legal
- As noninvasive or nondestructive in nature
- Not always the case
- Read your ISP’s “Acceptable Use Policy”
Federal Laws
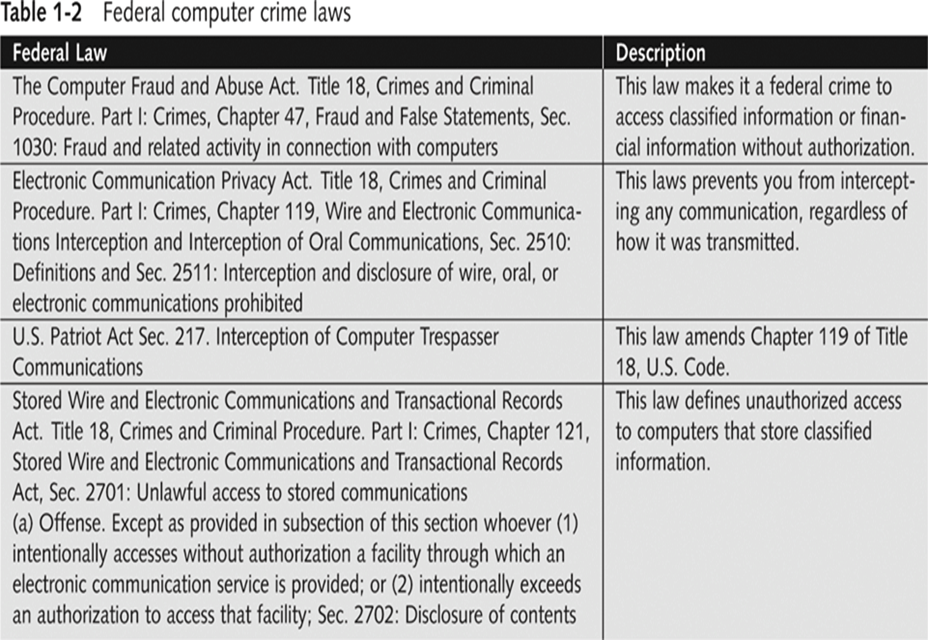
- Federal computer crime laws are getting more specific
–Cover cybercrimes and intellectual property issues
- Computer Hacking and Intellectual Property (CHIP)
–New government branch to address cybercrimes and intellectual property issues
Objectives
- Ethical hacking
- What you can do legally as an ethical hacker
- What you cannot do as an ethical hacker
What You Cannot Do Legally
- Accessing a computer without permission is illegal
- Other illegal actions
–Installing worms or viruses
–Denial of Service attacks
–Denying users access to network resources
- As an independent contractor (ethical hacker), using a contract is just good business
–Contracts may be useful in court
–Internet can also be a useful resource
–Have an attorney read over your contract before sending or signing it
Ethical Hacking in a Nutshell
- What it takes to be a security tester ?
–Knowledge of network and computer technology
–Ability to communicate with management and IT personnel
–Understanding of the laws
–Ability to use necessary tools

